page 20
Note: the contents of this page as well as those which precede and follow, must be read as a continuation and/or overlap in order that the continuity about a relationship to/with the dichotomous arrangement of the idea that one could possibly talk seriously about peace from a different perspective as well as the typical dichotomous assignment of Artificial Intelligence (such as the usage of zeros and ones used in computer programming) ... will not be lost (such as war being frequently used to describe an absence of peace and vice-versa). However, if your mind is prone to being distracted by timed or untimed commercialization (such as that seen in various types of American-based television, radio, news media and magazine publishing... not to mention the average classroom which carries over into the everyday workplace), you may be unable to sustain prolonged exposures to divergent ideas about a singular topic without becoming confused, unless the information is provided in a very simplistic manner.
Let's face it, humanity has a lousy definition, accompanying practice, and analysis of peace.
On page 17 we did a cursory introduction of the "fast and slow" thinking thesis of Daniel Kahneman and Amos Tversky, and deliberately left ourselves open to refutation by some readers who... acting as the greedy Capitalist's they are, plunge into an intellectual opportunity that they think will be profitable to their overall conceptualizations about thinking; and will be able to fortify their position by acquiring the intellectual arms and ammunition of another for their own uses. Yep, like so many who are vulnerable to being sucked into the action of a herd mentality, there is a crowd of fans having joined in the chorus due to the "Thinking, fast and slow" idea that is reminiscent of a side show selling its snake oil salve to be used in a presumed behaviorist approach that will help to yield a pecuniary profit. Yet, all that is being shown is that educated people can act like small town hicks whose main education has been culled from hearsay and the family bible.
Because of Kahneman's living and working exposure to a culture suffused with a prominent religious orientation... even if he were to claim being an atheist; it is necessary to examine the fast/slow thesis from the old religious bad/good or evil/good association. The two-system represents humans as using a two-patterned scaffolding from which is built an over-riding two-divisioned architecture as if there were a two-patterned blue-print. This is ridiculous!, especially given the fact that our anatomy and biology having developed as an adaptive form of evolution on a decaying planet is particularly three-patterned based, as cited on page 3 in this series, ... and is being used to describe human behavior in a bad/good or impulsive, reflexive, instinctive versus methodical, reflective, intelligent; yet the pattern-of-three presence is being brushed aside or simply not known. So many idiot Economists and Psychologists are not even aware of Tripartite Ideology except for perhaps in some childish reference to theology, children's literature, Dumezilian advocacy, numerology, or as someone's favorite number.
The "Thinking, Fast and Slow" thesis uses the old good/evil theme by flip-flopping the arrangement to read as "evil/good" in the form of "fast/slow" defined with terms which appeal to those who see themselves in a smart/dumb, rich/poor, right/wrong, professional/non-professional, etc... world. No doubt many of them view the dichotomy of peace/war (conflict) as if it were an irrefutable axiom... all because they see the world in a predominant two-patterned fashion. They have not taken the time to exam the presence of how many and diverse patterns-of-three are. Their logic is two-based whereas logic contains a dichotomy from which an emerging trichotomy is evident, such as seen in the following examples:
- [{Thesis/Anti-thesis}- Synthesis] of Hegelian fame.
- [{Major Premise/Minor Premise} Conclusion]
- [{Red/Green}- Yellow] street lights
- [{Hot/Cold}- Warm]
("Figure") in logic, (is) the classification of syllogisms according to the arrangement of the middle term, namely, the term (subject or predicate of a proposition) that occurs in both premises but not in the conclusion. There are four figures:
In the first figure the middle term is the subject of the major premise and the predicate of the minor premise; in the second figure the middle term is the predicate of both premises; in the third figure the middle term is the subject of both premises; in the fourth figure the middle term is the predicate of the major premise and the subject of the minor premise. All standard syllogisms may be described by designating their figure and mood: In logic, ("mood" is) the classification of categorical syllogisms according to the quantity (universal or particular) and quality (affirmative or negative) of their constituent propositions. There are four forms of propositions: A (universal affirmative), E (universal negative), I (particular affirmative), and O (particular negative). Because each syllogism has three propositions and each proposition may take four different forms, there are 64 different patterns (moods) of syllogisms. Twenty-four of the 64 possible moods are valid, though only 19 were traditionally accepted as valid. Various mnemonic terms are employed to label these moods. The vowels of these terms represent the forms of propositions in the syllogism. For example, "Felapton" is the mnemonic term to signify the mood in which the major premise (the premise containing the predicate of the conclusion) of the syllogism is an E proposition, the minor premise (the premise containing the subject of the conclusion) is an A, and the conclusion is an O. Sources: "Figure."/"Mood." Encyclopædia Britannica Ultimate Reference Suite, 2013.(Please note the "64" value and correlate it with the "64" in amino acid distribution, the I-ching and let us add the colloquialism: "That's the 64 dollar question"... all of which exhibit the same pattern which can be broken down into simpler patterns... but that in identifying such patterns, some readers may be inclined to think in terms of some "Universality" when what is actually being expressed is a conservation effect produced by human physiology under incrementally deteriorating environmental conditions.) |
And though many readers are well aware of this pattern-of-three but are inclined to see the world in a monocular form of bifurcation. It's like looking through a telescope connected to a set of binoculars instead of through the binoculars into a telescope with variable lens magnifications like a stereoscopic microscope. Whereas with a microscope one can change lens magnifications and filters, the "pattern-of-two" becomes a fixed magnification and filtering mechanism whereby we have institutions such economics, religion, governments, Nobel Peace Prize committee, United Nations, etc., that act like different role models but they are teaching the same underlying two-patterned lesson.
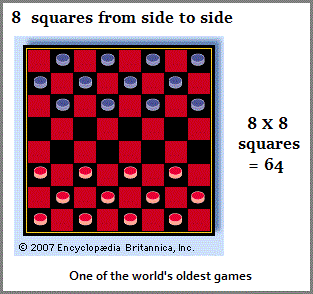
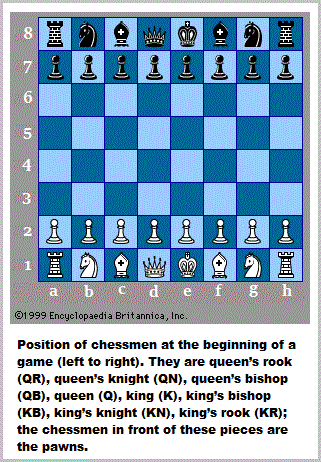
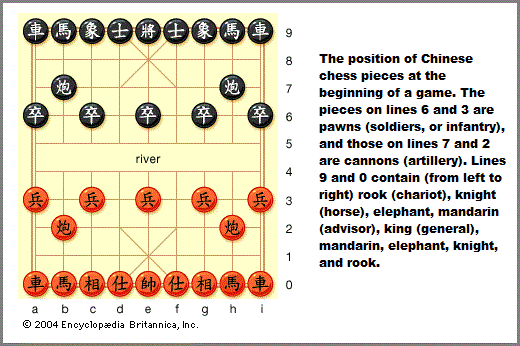
With respect to the "64", it too may be found in the number of squares on a Chessboard and Checkersboard, but it is not on the presented Chinese Chessboard, despite the wide-spread presence of the "64" idea in the Chinese I-Ching philosophy.
 |
 |
 |
|
Because playing chess is thought to exhibit some fundamental type(s) of thinking, it has a history of being applied to the development of computer programming. A short history review might be helpful to some readers:
Master search heuristics (Heuristics: A common-sense rule (or set of rules) intended to increase the probability of solving some problem. (Wordweb definition #2)) The ability of a machine to play chess well has taken on symbolic meaning since the first pre-computer devices more than a century ago. In 1890 a Spanish scientist, Leonardo Torres y Quevado, introduced an electromagnetic device—composed of wire, switch, and circuit—that was capable of checkmating a human opponent in a simple endgame, king and rook versus king. The machine did not always play the best moves and sometimes took 50 moves to perform a task that an average human player could complete in fewer than 20. But it could recognize illegal moves and always delivered eventual checkmate. Torres y Quevado acknowledged that the apparatus had no practical purpose. As a scientific toy, however, it gained attention for his belief in the capability of machines to be programmed to follow certain rules. No significant progress in this area was made until the development of the electronic digital machine after World War II. About 1947 Alan Turing of the University of Manchester, Eng., developed the first simple program capable of analyzing one ply (one side's move) ahead. Four years later a Manchester colleague, D.G. Prinz, wrote a program capable of solving mate-in-two-move problems but not actually playing chess. A breakthrough came in 1948, when the research scientist Claude Shannon of Bell Telephone Laboratories in Murray Hill, N.J., U.S., presented a paper that influenced all future programmers. Shannon, like Torres y Quevada and Turing, stressed that progress in developing a chess-playing program would have a wider application and could lead, he said, to machines that could translate from language to language or make strategic military decisions. Shannon appreciated that a computer conducting an entire game would have to make decisions using incomplete information because it could not examine all the positions leading to checkmate, which might lie 40 or 50 moves ahead. Therefore, it would have to select moves that were good, not merely legal, by evaluating future positions that were not checkmates. Shannon's paper set down criteria for evaluating each position a program would consider. This evaluation function is crucial because even a rudimentary program would have to determine the relative differences between thousands of different positions. In a typical position White may have 30 legal moves, and to each of those moves Black may have 30 possible replies. This means that a machine considering White's best move may have to examine 30 × 30, or 900, positions resulting from Black's reply, a two-ply search. A three-ply search—an initial move by White, a Black reply, and a White response to that—would mean 30 × 30 × 30, or 27,000, different final positions to be considered. (It has been estimated that humans examine only about 50 positions before choosing a move.) Turing's evaluation function was dominated by determining which side had more pieces in various future positions. But Shannon suggested that each position could be weighed using positional criteria, including the condition of pawns and their control of the centre squares, the mobility of the other pieces, and specific cases of well-placed pieces, such as a rook on an open (pawnless) file or on the seventh rank. Other criteria were used by later programmers to refine and improve the evaluation function. All criteria had to be quantified. For example, a human master can quickly evaluate the mobility of bishops or the relative safety of the king. Early programs performed the same evaluation by counting the number of legal bishop moves or the squares under control around a player's king. Andrew E. Soltis: Columnist, Chess Life. Chess columnist and reporter, New York Post. Author of Pawn Structure Chess and many others.Source: "Chess." Encyclopædia Britannica Ultimate Reference Suite, 2013. |
And the fact that Kahneman got a Nobel prize only means that the Nobel committee are just as prone to believing in a reproduction of an old theme (good/evil) cast into a new role with a new script. Thousands upon thousands of people bought into accepting and sometimes selling an old snake oil presented in a new package. For all your presumed sophistication and system 2 thinking, you have shown yourselves to be a system 1 adherent... because most people have not surveyed multiple subjects deliberately looking for underlying basic patterns and then association them with brain hemispheric attributes which fully indicate the existence of a dichotomous/trichotomous arrangement. Let us once again provide a sampling of hemispheric attributes and their patterned formulation by referring to page 6 in this series. The examples can be found about halfway down the page. One should also note that the inclined three-patterned left hemisphere appears to attempt to organize two-patterned information into groups of three and the right hemisphere appears to attempt to organized three-patterned information into groups of two.
Like many a religious person who likes to think (unboastfully) of themselves as being good... to believe they incorporate a "necessary" level of humility or they will be punished by God for exhibiting an unworthy fidelity to a given belief and/or belief system; economists like to view themselves in the same manner though their "god" has the added letter "l" and is portrayed as "gold". Yes, by all means, let us attempt to peer back into the distant past (before the 12th Century) and attempt to locate the developmental association between the western usage of the word god and the word gold and thus identify amongst which god-obsessed people arose the occupation of "goldsmith" whose correspondence with the initial visual referencing became more and more obscured by commercial indulgences, though in a comparative vien of liberal thinking one might well attribute the word "godsmith" to clergy. If the stark resemblance between parent and child is not believed when one takes into account the golden Sun and its ancient interpretation as the visage of a radiating (effulgent) god sometimes spelled "Son" instead of "Sun"... that was transferred onto the image of a man who was given the title "Son of god" in even more ancient times; one might well overlook the zealousness, the fanaticism, the hoarding, and the relationship between some individuals and communities and their obsession with the ownership of gold as a vicarious representation of their oneness with a god in a form of accepted social transference of identity.
.Yes, use an analytical technique of historically reflective detection as a substitute form of DNA analysis so that the disbelief you impulsively grasp for in the presence of such a reflection can reach out and slap you in the face. It's time to wake up from your economic dream worlds that have been used to substitute underlying religious themes with— themes which are themselves little more than illusory representations of more fundamental environmentally influenced biological patterns coincident with the cyclicities of a planet that is on an incremental course of decay and taking every thing with it... so long as it remains on the planet. Unfortunately, humanity falls prey to so many side shows like the Thinking, Fast and Slow carnival act that humanity may never take the time to look past its self-absorptions in order to evacuate the planet instead of leaving behind Voyager 1 and 2 as a remnant of a species whose impulse in using patterns-of-two were confused with an intelligence undergoing the development of an emerging pattern-of-three formulation. Humanity itself must be the third Voyager. We must force ourselves past the inclinations for two-patterned thinking.

Image and information source: "Voyager." Encyclopædia Britannica Ultimate Reference Suite, 2013.
Let us provide some additional patterns-of-two examples so that no reader cannot begin to suggest that we are attempting to conceal the existence of a recurrence that they might wish to use as supportive evidence in their presumption for THE major pattern of mental organization nor that there aren't such a variety as to forego providing them with a necessary sampling (that they may not be aware of) in order that we may assert the existence of a recurring two-structured mental pattern from different perspectives. A sampling of hemispheric attributes and their patterned formulation by referring to page 6 in this series. The examples can be found about halfway down the page. One should also note that the inclined three-patterned left hemisphere appears to attempt to organize two-patterned information into groups of three and the right hemisphere appears to attempt to organized three-patterned information into groups of two.
|
Analytic Learners Like:
Could develop...
|
Global Learners Like:
Could be...
|
| ***With respect to the reference in the Left Hemisphere column about seeing in black and white, this author appears to have not taken into consideration the ideas of singularity, duality, and Triplicity. | |
Many gifted children go unrecognized simply because they are operating with a brain dominance at odds with their parents and teachers.
Schools have traditionally valued children who learn well by sitting still, listening, speaking, reading and writing as directed, as being cleverer than those whose brain layout favours a different style of learning.
Logical, verbal, organized left-brain dominants (many of our teachers) find many right brain characteristics sloppy, careless, irrational and unfocused. So thousands of highly gifted, creative, original, very clever children are labeled as lazy, limited and "just average".
http://www.teacher.co.nz/bookrevi.htm
| LEFT BRAIN
FUNCTIONS uses logic detail oriented facts rule words and language present and past math and science can comprehend knowing acknowledges order/pattern perception knows object name reality based forms strategies practical safe |
C O R P U S C O L L O S U M |
RIGHT BRAIN
FUNCTIONS uses feeling "big picture" oriented imagination rules symbols and images present and future philosophy & religion can "get it" (i.e. meaning) believing appreciates spatial perception knows object function fantasy based presents possibilities impetuous risk taking |
| REPTILIAN BRAIN | ||
| BRAIN STEM | ||
http://www.viewzone.com/bicam.html
As an alternative view to dividing the brain in Right and Left, as an extension of the idea that men and women process information differently due to differences in the structures of their brain, take a look at the following two charts which illustrate the differences in Males and Females within the context of a religious perspective:
| According to the Bible, man and woman are alike in spirit, but not in soul and body. (For this reason the term "man" or "brothers" is often generic in the Bible when doctrinal teaching is in mind). The physical, anatomical differences between the sexes are well known. However man and woman are also quite different as far as the soul is concerned. One possible way of differentiating between men and women in terms of priorities and specialties is suggested by the following table. God has built a vast wealth of variety and diversity into the human gene pool. Many variations in physical characteristics as well as some personality and emotional characteristics are governed by genetic factors. In terms of behavior, there are wide ranges in what can be considered normal masculinity and femininity. | |
| MASCULINITY LOGOS |
FEMININITY SOPHIA |
| Paternal Instincts Leads, takes charge Initiates: Hunts, Ranges, Thrusts Values logical thinking, Logos-centered mind Bases decisions on reasoning more than emotions or intuition Assertive, aggressive, outgoing towards the world Provides outside support and protects (as a soldier) Feels ill-at-ease in passive, receptive roles May under-value importance of emotions and intuition Specialist in "Doingness," "Withoutness" Mechanistic, scientific, digital-thinking Divided left and right brain |
Maternal
Instincts Responder Follower Nestles, nurtures, shelters, traps heals Values emotions highly, relationship orientation Heightened intuitive ability and perception Sophia-based thinking At ease in a passive, receptive role Takes leadership with difficulty when male leader defaults Natural concern for the present quality of life Specialist in "Beingness" and "Withinness" Artistic, creative, analog thinking More unified left and right brain, holistic thinking |
As with any information, one must take into account the sex, age, and overall demographics of the person(s) making the compilation.
| The human race is fallen, self-centered, corrupted and mortally damaged by the sin of Adam. All aspects of our humanity have been affected. For the sake of discussion one can make a table of what might be considered archetypal aspects of our fallen sexuality. The table below is suggested as a model for discussion purposes and is not a description of specific men or women, obviously! | |
| NEGATIVE MASCULINITY | NEGATIVE FEMININITY |
| Beast-like Authoritarian, domineering, ruthless, despotic Lords it over others Devalues importance of emotions Overly logical, methodical, rigid Cold, indifferent, impersonal, unapproachable Demands respect of subordinates Intimidates others or rules them by fear Unforgiving, and unwilling to be a team-member Boring, unimaginative, overly self-controlled Overly logical, unable to be spontaneous Willing to compromise to gain position or power A beast, tyrant or a despot |
Harlot-like Possessive, controlling, Manipulative, contriving Irrational in rejecting logic, emotionally controlled Gives love or affection but extracts a price Selfishly concerned with appearances and prestige Entraps others for her own purposes Demands attention and recognition A witch, sorceress or seductress |
http://www.ldolphin.org/Image.html
The following example is a re-adapted view of the brain's divisions, parts, and some would say functions, into an overall 3-patterned division with sub-divisions.
| PRIMARY | SECONDARY | TERTIARY | ||
| ¯ 3 Section Division |
¯ General Primary Division |
¯ Constituent Parts Division |
¯ Functional Brain Division |
¯ Developmental Division |
| Forebrain ® |
Cerebral Hemispheres | Cerebral cortex: Frontal Lobes Temporal Lobes Parietal Lobes Occipital Lobes Corpus Callosum |
Neocortex | Telencephalon |
| Amygdala Hippocampus Basal ganglia: Caudate Nucleus Putamen Globus Pallidus |
Limbic: Cingulate Cortex Amygdala Hippocampus Septum | |||
| Thalamus Hypothalamus |
Diencephalon | |||
| Midbrain ® |
Midbrain: Superior Colliculus Inferior Colliculus |
Brainstem | Mesencephalon | |
| Hindbrain ® |
Cerebellum Pons |
Brainstem | Metencephalon | |
| Medulla Oblongata | Myelencephalon | |||
| Spinal Cord | ||||
Information was liberally adapted from:
http://www.childtrauma.org/brain_I.htm
Date of Origination: Tuesday, 27-Dec-2016... 02:23 AM
Date of initial posting: Monday, 2-Jan-2016... 10:37 AM
Updated posting: Friday, 6-April-2018... 121:06 PM